DMARC: Beginner’s guide
Are you familiar with all email providers for your domain? Are spammers attempting to fake your email domain in order to exploit security flaws or commit fraud? To ensure delivery to inboxes, are you adhering to the suggested email best practices? These are the inquiries that DMARC responds to, providing you with complete control over email delivery for the domain of your business.
What is DMARC?
Domain-based Message Authentication, Reporting, and Conformance (DMARC) is the name of an email authentication protocol. It intends to empower domain owners to prevent email spoofing and other illegal uses of their domains.
preventing the use of a domain in phishing, email scams, business email compromise, and other cyber threat activities. It is the goal and the major result of implementing DMARC.
Receiving email servers authenticate incoming emails using domain owner’s instructions in the DNS record. The email will be delivered and trustworthy if the authentication process is completed. Depending on the instructions in the record, the email may be sent, quarantined, or denied if the test fails.
Why do we need DMARC for email?
There is no channel that has a broader reach than email, with approximately 5 billion email accounts globally. This makes it certain that cyber criminals choose to use this channel for nefarious ends. Despite recent additions to the security mechanisms protecting this channel, crime on it is continuing on the rise year after year. 95% of hacking efforts and data breaches involve email.
Implementing effective security controls against fraudulent emails enhances delivery, increases brand dependability, and provides domain owners with visibility into their domain usage.
The initial use case for DMARC was email fraud. It allows for the monitoring of a domain’s usage and prevents unauthorized senders from sending emails on behalf of an organization.
Email reliability is essential to organizations. The first step in fixing email delivery problems is frequently to implement DMARC, which is the cornerstone for dependable email delivery.
It is becoming more and more necessary in order to comply with industries, governments, and regulations. Additionally, several cybersecurity insurance companies are starting to demand it.
Implement DMARC to maximize the benefits of using email.
What do DKIM & SPF have to do with DMARC?
I guess everything. The ISP is in charge of deciding what to do with the results of SPF and DKIM. Based on the findings from DKIM and SPF, DMARC goes a step further and offers you complete control to define a policy to reject or quarantine emails from sources you do not know or trust.
For instance, PayPal publishes a DMARC record that states to reject the message if DKIM or SPF is unsuccessful because PayPal is a major target for email fraud. Participating ISPs will review this policy and delete any unsuccessful emails. According to a report by Agari, DMARC assisted PayPal in preventing an estimated 25 million attacks during the 2013 holiday season.
In summary, DMARC enables you to direct ISPs as you choose how you want them to behave if SPF and DKIM fail or are not present.
What are DKIM and SPF?
Understanding the DKIM and SPF email authentication standards is a prerequisite for understanding the DMARC protocol. Given that DMARC is built upon these standards, let’s first go over them.
DomainKeys Identified Mail (DKIM)
It is a technique for verifying the legitimacy of email messages. Before sending, sign each email with a private key, then verify it using a public key stored in DNS. By doing this, it can be confirmed that the message was not changed in route.
An ISP (such as Gmail) can examine the message and determine if it remains unchanged since delivery.
In other words, it stops someone from stealing your email, changing it, and then sending it along with fresh (potentially false) information. ISPs use this data to establish a reputation for your domain, which is another little-known advantage of DKIM.
Excellent sending practices (no spam, bounces, high engagement) will help you gain the ISPs’ trust and enhance your reputation.
Each email you send using DKIM is signed using the private key kept on your mail server. By retrieving a corresponding public key from a unique DKIM record in your DNS, later ISPs can check the authenticity of a message. The public key check only accepts messages signed with your private key using the same cryptography as SSL.
Sender Policy Framework (SPF),
It is an email authentication standard, is utilized In order to prevent phishing attempts. It enables your business to decide who is permitted to send emails on your domain’s behalf. In a typical phishing attempt, the threat actor spoofs the sender’s address to appear as an official corporate account or someone the victim may know. This makes it helpful.
You need it for things like support (Zendesk, Helpscout, etc.) or other service providers who send emails on your behalf, in addition to using it for corporate email accounts or email marketing.
What is a DMARC Record?
The DNS database of an organization has a DMARC record. A DNS TXT record with the specific identifier “_dmarc.mydomain.com“ is a specially formatted variant of a DMARC record.
It is how a DMARC record appears. “v=DMARC1; p=none; ruf=mailto:[email protected]; ruf=mailto:[email protected]; pct=100“
This document reads as follows left to right in plain English:
- p=none defines the preferred treatment, or DMARC policy,
- while v=DMARC1 Indicates this is a DMARC record.
- The mailbox to which aggregate reports should be sent is rua=mailto:[email protected].
- The mailbox where forensic reports should be transmitted is ruf=mailto:[email protected].
- The percentage of mail to which the domain owner wants to apply its policy is pct=100.
How does DMARC work?
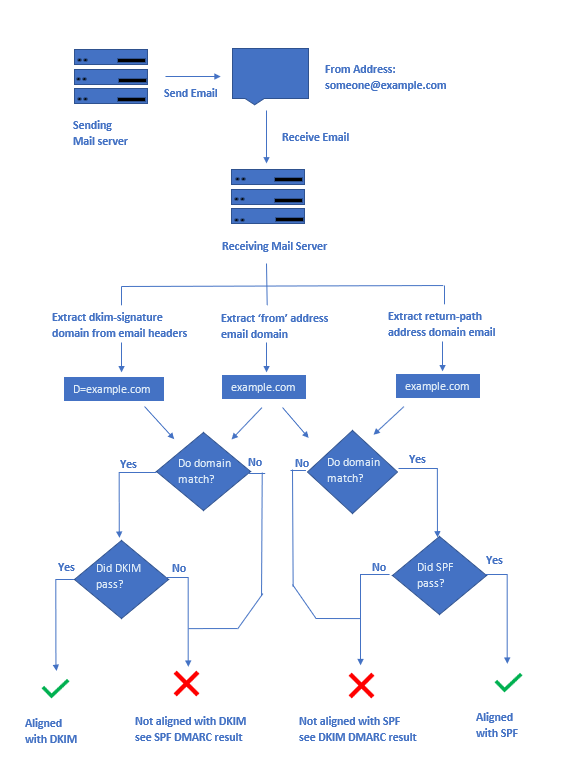
SPF, DKIM, and DMARC are used along with the authentication tests we previously described in order to authenticate a message and determine what to do with it.
In essence, a sender’s DMARC record advises a recipient of what to do in the event that they get a suspicious email purporting to be from a specific sender, such as ignore it, quarantine it, or reject it.
The process is as follows:
- At their DNS hosting business, the domain owner posts a DMARC DNS Record.
- The receiver mail server checks to verify if the domain has a DMARC record when an email is delivered by the domain (or someone spoofing the domain).
- The mail server then runs DKIM, SPF, and alignment tests to confirm that the sender is indeed the domain it claims to be.
- Has the communication been properly signed with a valid DKIM signature?
- Does the sender’s IP address match those listed in the SPF record as approved senders?
- Do the domain alignment tests on the message headers pass?
- The mail server is now prepared to apply the DMARC policy for the sending domain with the DKIM & SPF findings. Basically, this policy states:
- If a message fails the DKIM/SPF tests, should I quarantine, reject, or leave it alone?
- The receiving mail server (think Gmail) will send a report on the outcome of this message and any additional mail they see from the same domain after deciding what to do with the message.
What are the benefits of DMARC?
You might want to use it for a few important reasons:
Reputation: By blocking unauthorized parties from sending emails from your domain, publishing a DMARC record safeguards your brand. In some circumstances, merely posting a DMARC record can lead to an improvement in reputation.
Visibility: By letting you know who is sending emails from your domain, DMARC reports improve the visibility of your email program.
Security: DMARC assists the email community in creating a uniform response strategy for communications that are unable to authenticate. This enhances the security and reliability of the email ecosystem as a whole.
Why DMARC is Crucial?
Without DMARC, you are signaling to hackers that your security posture is weak, which encourages them to target your digital assets. If you haven’t implemented DMARC, your DNS is already pointing out security flaws. Your Cyber Security Rating includes the DMARC parameter, which is crucial.
- The average cost of a spear phishing attack on a company is $1.6 million.
- Phishing scams result in annual losses of $500 million.
- An average company with 10,000 employees must pay to deal with phishing attempts. $1.75 billion annually
- The typical worker loses 4.16 hours per year to phishing schemes.
- Only 3% of users will notify management about phishing emails.
- BEC scams target more than 400 firms each day.
- In 2016, 76% of firms claimed to have fallen victim to a phishing attack.
- Companies that acknowledged falling prey to phishing attacks in 2016 include: 76%
- CEO email fraud has affected one out of every three businesses.
- 70% of emails sent worldwide are malicious
Conclusion
Emails can be sent from a domain until Email Authentication protocols like DMARC secure it.
It is essential to implement Email Authentication protocols to make sure that only “you” can send email.
As a result, by using DMARC to secure your domain, you effectively safeguard the reputation and brand of your business.

Leave a Reply
Want to join the discussion?Feel free to contribute!